Tyler Combs

Key Takeaways
Increasing digitization and the primacy of information in the modern economy has made effective cybersecurity vital for law firms to fulfill their role as custodians of clients’ legal information. As a result, data breaches and ransomhack attacks which turn into data breaches are the greatest cybersecurity risk the industry faces.
Law firms face severe financial and reputational harm from cyberattacks in the form of ransomware attacks and data theft. Such attacks risk eroding firms’ trustworthy image among current and prospective clients. The image which is existential for the legal industry operation.
To protect against these threats, law firms must upgrade their incident response capabilities, ensure that qualified people are in place, bridge the gap in employee knowledge on basic cybersecurity practices, and stay vigilant regarding continuing and emerging threats.
By addressing the top-three threats to the industry - ransomware, DarkWeb exposure, and botnet intrusions, AdvIntel loss avoidance services can directly facilitate these objectives.

Background
The increasingly central role of digitization and information in the economy has made effective cybersecurity vital to business operations, and the legal industry is no exception. Across fields as diverse as personal injury, employment, tax, and intellectual property, law firms serve as custodians of highly sensitive information for their clients. As a result, it is imperative that they maintain adequate cybersecurity protocols and procedures in order to protect this information and uphold the trust their clients have placed in them. Failure to do so can have severe repercussions for a firm’s clients, and in turn, the firm’s reputation.
Recent cases of cyberattacks against law firms illustrate the scale and ripple effects. For instance, in September 2020, one actor gained access to files containing I-9 employment authorization forms and was able to access the names, phone numbers, email addresses, dates of birth, Social Security numbers, and passport numbers of an undisclosed number of current and former employees of a law firm’s client; all information that could be used for identity theft. As part of its recovery from the attack, the law firm offered free credit monitoring services to all the affected customer’s employees - a costly and complicated process.
This case is not unique - the American Bar Association reveals that 29% of the respondents to a survey on law firm cybersecurity experienced breach-related threats in 2020, but only 34% of firms maintain cybersecurity incident response plans. It is therefore crucial for both firms and clients to have an accurate picture of the cyber threats facing the legal sector.
Investigative Insight - DarkWeb Shadow Economy
Law firms face a highly complex risk environment.
A variety of threat actors using myriad tools, tactics, and procedures lurk in the wings, searching for opportunities to exploit the legal industry for their own gain.
A survey of DarkWeb activity tracked by AdvIntel’s Andariel provides snapshots of how threat actors monetize their exploitation of law firms. Often, this is achieved by gaining access to a firm and then selling that access.
For example, in the below post made on the top-tier DarkWeb forum from June 14, 2020, the threat actor “piratecap” (alias obfuscated) offered to sell access at the domain administrator-level to a law firm/legal services provider valued at $24 million USD in revenue. They set the starting offer at $500 USD.

Post by threat actor “piratecap” (alias obfuscated) offering to sell domain administrator access to an unidentified law firm/legal service provider on DarkWeb forum (Source - AdvIntel’s Andariel Platform - DarkWeb Collection)
In harvesting and selling access, threat actors such as piratecap are able to make a relatively quick and low-investment profit, as they only have to conduct enough reconnaissance to get the necessary credentials before moving on to the next target. However, while this initial threat actor may not directly exploit their target, their business model is predicated on having a “consumer market” of threat actors who do wish to engage in deeper exploitation and are willing to purchase the access piratecap is selling. The inclusion of the revenue estimate indicates that this law firm/legal service provider is a target of substantial value, which provides threat actors with further temptation to purchase this access.
A similar pattern is seen in this sale offer, posted on October 28, 2020, by the threat actor “whisper” (alias obfuscated). In the post, they offer to sell access to an entity in the corporate law and advocacy sector, and which includes access to twenty-five hosts in the target entity’s network. Between the twenty-five hosts and the $1,000 USD starting ask, this is likely a significantly higher level of access than that offered by piratecap, and would facilitate a much greater degree of damage to this legal entity is sold.

Post by threat actor “whisper” (alias obfuscated) offering to sell access to twenty-five hosts in the network of an unidentified corporate law and advocacy entity on DarkWeb forum (Source - AdvIntel’s Andariel Platform - DarkWeb Collection)
However, many threat actors do not stop at selling access. Take this post by the threat actor “moneyrain” (alias obfuscated), posted to a DarkWeb forum on October 13, 2020. In the post, moneyrain offers to sell documents belonging to a U.S. law firm at an asking price of $1,500 USD. Notably, they specify that the bundle includes tax forms and confidential client documents, both private and highly sensitive forms of information. Moneyrain has gone beyond the monetization of access seen in the discussion of the two above actors, and has instead stolen the law firm’s private information and is marketing it for sale.

Post by threat actor “moneyrain” (alias obfuscated) offering to sell confidential documents from an unidentified law firm on DarkWeb forum (Source - AdvIntel’s Andariel Platform - DarkWeb Collection)
This post provides a vivid example of how threat actors monetize data exfiltration from law firms. As discussed previously, one of the primary tasks of a law firm is managing and protecting a client’s private legal information. Knowing this, threat actors such as moneyrain seek out this information when penetrating a law firm's network, steal it, and offer it for sale on DarkWeb forums and marketplaces. From there, other threat actors can purchase the data for their own purposes and plans. Depending on the legal documents offered, threat actors could use the information for such activities as fraud, espionage, and blackmail, all severe risks for an individual or firm that are directly rooted in the compromise of their legal services provider.
Investigative Insight - Ransomware Raiders
The case of a ransomware attack against a law firm illustrates how these dangers come to a head. In the spring of 2020, a ransomware group launched an attack on the firm, likely by using a remote desktop protocol vulnerability to upload their malware. The gang stole a large amount of confidential client information and threatened to release it unless a large ransom was paid. Later, the group began auctioning off the data of individual clients. This incident vividly demonstrates how threat actors target and exploit law firm’s central client data to extort them.
Law firms are especially susceptible to these types of attacks. This vulnerability is due to ransomhack instructions in which a syndicate demands a ransom for not publishing stolen information rather than offering decryption keys is becoming the new normal for locker operations. These types of attacks originated when the crime groups started to exploit the fragile fabric of social relationships and reputational networks. Law firms and their customers are at the center of this ecosystem, as the concepts of trust, ethics, and morals are central to their business. REvil , one of today's most prolific ransomware gangs, openly stated that the future of ransomware lies in exploiting trust by threatening the victim with the publishing of confidential information. And just like REvil, who was behind the infamous attack against Grubman Shire Meiselas & Sacks, ransomware gangs know that law firms are the most vulnerable target for this exploitation.
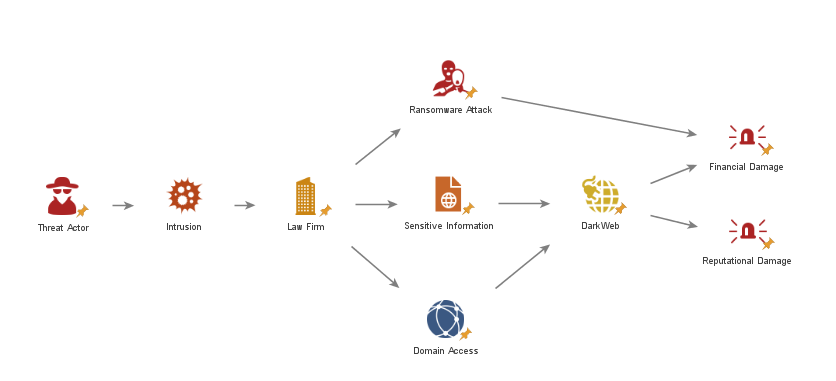
Maltego visualization of event chain in law firm cybersecurity breach (Data Source - AdvIntel’s Andariel Platform - DarkWeb Collection)
Investigative Insight - Botnet and RDP Infiltration
In addition to DarkWeb forum activity, AdvIntel analysts have tracked frequent botnet infections of law firms. As of writing, AdvIntel has identified 271 botnet infections of entities in the legal sector since March 2020. Many botnets, including those tracked by AdvIntel, are modular tools that can exploit targets in a variety of ways designed to steal as much information as possible. For example, botnets with trojan components can be used to steal important information and credentials, such as personal identifiable information (PII) and banking credentials, which can then be used for further theft, blackmail, or fraud. Meanwhile, botnet-loaders can upload a variety of malware strains into a target network, including ransomware.
The ransomware loading capability of botnets is of particular concern, as all the botnets tracked by AdvIntel operate in conjunction with prolific ransomware gangs. In these partnerships, the botnet group provides the initial access that the ransomware gang uses to deliver their payload, with profits from the ransom split between the two groups. This model is employed by some of the most high-profile groups; for example, by the Ryuk group that has attacked some of the largest companies in the world. As a result, botnet-ransomware liaisons are some of the most dangerous threats that could exploit the legal sector, particularly large firms.
In one intrusion investigated by AdvIntel, a prolific botnet made significant inroads into a major, global intellectual property law firm with numerous major clients across the finance, technology, and retail sectors. At the time of detection by AdvIntel’s HAWK Botnet Compromise Prevention System, the operators had gained access to 2000 hosts in the target’s network and made an estimate of its revenue in the hundreds of millions USD. This indicates that the operators were likely planning further exploitation of the law firm and had gained the means to do so through control of thousands of devices in the firm’s network.
In a firm with multi-hundred million dollars in revenue, this is a potential herald of a major ransomware attack or even a hack-and-sell operation of the sort executed by REvil against Grubman Shire Meiselas and Sacks.
However, botnet operators do not only target large firms. In another case, the same botnet infected a local law firm on the West Coast with a revenue of only several million. The operators made note that they had infected the firm’s primary domain and assigned it to their high-value target list, indicating that they have an interest in the entity. While smaller firms such as this are not at as high a risk of ransomware attack by the major groups, smaller groups may extort them for several thousand dollars.
On top of botnets, ransomware gangs also penetrate and exploit law firms through compromised remote desktop protocol (RDP) credentials. By exploiting this access, the threat actors gain control over devices in a law firm’s network without the need to cooperate with a botnet gang. Such credentials can be obtained through a variety of methods. Some threat actors employ a brute-force method of entering a variety of username and password combinations until access is achieved. However, RDP credentials can also be purchased in DarkWeb marketplaces. For example, since November 2020, AdvIntel has identified the RDP credentials of 17 law firms offered for sale in top-tier DarkWeb marketplaces.
One recent case of a ransomware attack against a major law firm illustrates the dangers of compromised RDP credentials. In the spring of 2020, a ransomware gang notorious for using RDP access as their initial attack vector launched an attack on the firm. The gang stole a large amount of confidential client information and threatened to release it unless a ransom in the tens of millions was paid. When the firm attempted to hold out, the group began auctioning off the data of the firm's individual clients. This case directly points to how compromised RDP access is abused by threat. Furthermore, it is a vivid example of how ransomware gangs exploit law firm confidentiality: by stealing and releasing the information, the gang sought to undermine the firm's reputation for trust and reliability with information.
Mitigation & Prevention
Despite the significant threats posed to the cybersecurity of law firms, there are strong steps the industry can take to protect itself. As mentioned previously, the American Bar Association’s 2020 cybersecurity report discovered that only 34% of respondent law firms had incident response plans in place. A valuable starting point, therefore, is having company procedures for reporting and recovering from cyberattacks. If attorneys are not aware of who to talk to when they have opened a suspicious email or notice important files are missing, and there is no individual charged with addressing these concerns, a firm will open itself to easy exploitation.
However, to prevent incidents in the first place, it is important to have qualified people in place who are knowledgeable about proactive cybersecurity. For the most part, large firms (those employing 100+ attorneys) have dedicated cybersecurity staff, but that number drops precipitously as the size of the firm decreases. Cybersecurity needs will vary considerably based on the size and resources of the firm, but regardless of size, it is essential that staff understand basic security measures. For many firms, this will likely require education on practices such as effective login credential management, identifying suspicious emails, and other low-cost and common preventative measures. This is particularly necessary given the relatively low number of legal professions with information technology backgrounds.
Lastly, it is vital that law firms stay informed on the threats facing them in the cyber realm. Through AdvIntel’s loss avoidance services, firms can have access to cutting-edge threat intelligence based on exclusive sources. Through our tracking of prolific botnets that affiliate with ransomware gangs and our monitoring of DarkWeb marketplaces, AdvIntel, and our Andariel platform provides law firms with dynamic information on the most dangerous and active threats facing them. We regard the legal sector as one of our priority sectors for intelligence collection and analysis and thus stand ready to assist law firms in maintaining a competitive edge against threat actors seeking to exploit them.
Advanced Intelligence is an elite threat prevention firm. We provide our customers with tailored support and access to the proprietary industry-leading “Andariel” Platform to achieve unmatched visibility into botnet breaches, underground and DarkWeb economy, and mitigate any existing or emerging threats.
Tyler Combs focuses on investigating prolific actors and conducts DarkWeb research within Advanced Intelligence Security & Development Team. He graduated from Indiana University with a Bachelor of Arts in Political Science and Russian and East European Studies. His interests span a wide range across the security realm, including cyber, international, and human security.