By Anastasia Sentsova, Andrew Mincin, & Yelisey Boguslavskiy

Three of the oldest and most elite DarkWeb forums were hacked over the past two months which led to the disclosure of the personal information of its members. A follow-up evaluation determined that one of these forums are currently inaccessible, which may be attributed to law enforcement or rival community actions. AdvIntel investigates the underground environment and open sources on a subject of intelligence related to the breach to uncover possible scenarios of attacks defined by the top-tier members of the Russian-speaking cybercrime community.
Executive Summary
AdvIntel uncovers adversarial perspective on possible scenarios of attacks on three of the oldest Russian-language forums: Exploit (breach not confirmed, but the forum was down), Verified, and Maza (Mazafaka).
Four of the main interpretations of the events observed to be discussed by the cybercrime community members include:
1) Hacktivists group efforts
2) US law enforcement actions as a reaction to a continuous ransomware threat from the Russian-speaking DarkWeb community
3) Internal showdowns between underground communities
4) Regional law enforcement effort
The review of the DarkWeb chatter and the adversarial perspective analysis can add crucial predictive insights into the new strategies, methods, and approaches which the DarkWeb community may undertake in order to reorganize and increase its anonymity and security.
This adversarial analysis enables the establishment of efficient preventive strategies utilizing the known weak points of the DarkWeb community social and technical infrastructures and assists in conducting advanced HUMINT operations and threat actor engagements.
Background
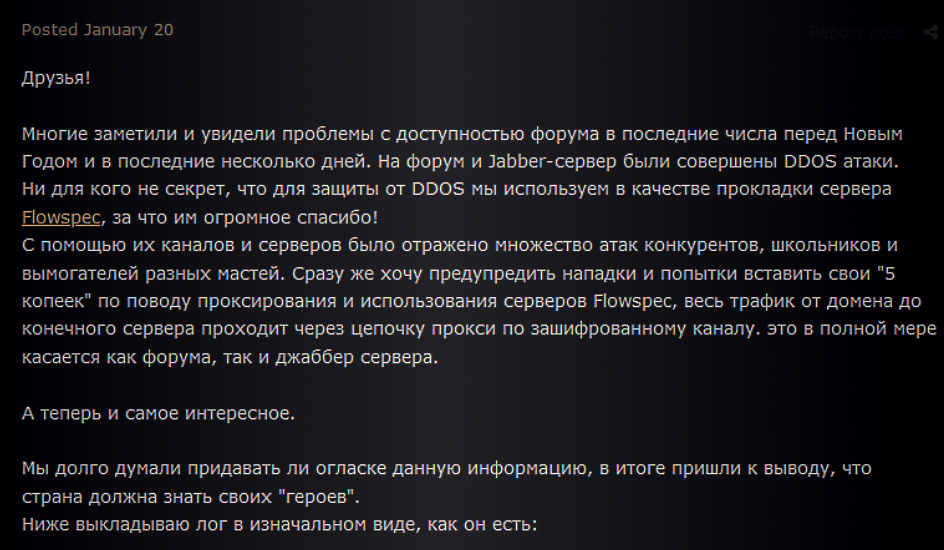
On January 21, 2021, the admin of the top-tier DarkWeb forum, Verified, operating under the alias “AdminSupport” (alias obfuscated), announced that the forum's BTC wallet was hacked and members' accounts might have been compromised. In addition, Verified’s database was observed to be offered on an English-language entry-level RaidForums on January 20, 2021, for $100,000 USD. Leaked data included member registration data, private messages, posts, and threads.
“Our BTC wallet was hacked, fortunately, we did not store large amounts there, but still the incident is not pleasant. The admin figured out the problem and now everything is OK. After clarifying the circumstances, the admin suggested that THEORETICALLY accounts on the forum might have been compromised (the probability is small, but it exists). In our business, it is better to play it safe and we decided to reset the codes for everyone. Just write them down and use it from now on.”
Admin of Verified forum announced hack of BTC wallet and possible compromise of forum members credentials on February 21, 2021
(Source: verified[.]ms)
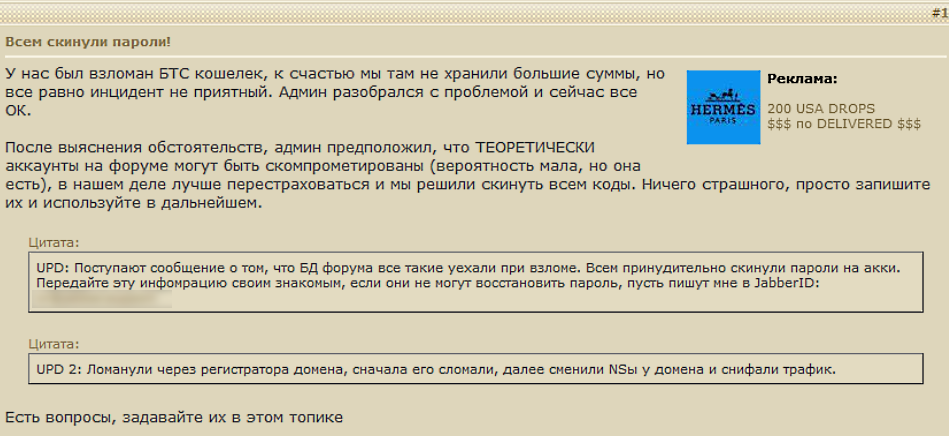
On March 1, 2021, an admin of the Exploit forum announced that on February 27, 2021, their monitoring system detected an unauthorized secure shell (SHH) access to a proxy-server of its hosting provider FlowSpec. This is used for protection from distributed denial-of-service (DDoS) attacks. Additionally, an attempt to dump network traffic was detected. This incident led to a blocking of the hosting provider account that has since been restored.
On March 3, 2021, the top-tier vetted Maza forum database was leaked on the DarkWeb containing more than 3,000 rows of the forum’s member data, including usernames, email addresses, and links to instant messengers, such as Skype, MSN, and Aim. While Exploit and Verified were brought back to life and seem to operate at a normal pace, the Maza forum is still observed to be down (at the time of this writing).
On March 4, 2021, an Exploit admin confirmed that the personal data of the forum members was not compromised and that servers are under constant supervision.

Exploit moderator confirmed that none of the forum members’ data were compromised on March 4, 2021
(Source: exploit[.]in)

Timeline of Verified, Exploit, and Maza DarkWeb forums breaches
(Source: AdvIntel)
These forum breaches resulted in the disclosure of cybercriminals’ personal information containing usernames, passwords, e-mails, and alternative channels of communication such as ICQ, Skype, Yahoo, and MSN that may be used for identity attribution.
Three main interpretations discussed across the DarkWeb include:
1) Hacktivist groups that announced the hack of underground forums on February 18, 2021
2) US law enforcement actions in response to attacks by Russian hackers on the US government and business sectors and as a reaction to a continuous ransomware threat from the Russian-speaking DarkWeb community
3) Internal showdowns between underground communities seeking a redistribution of power to establish control over forums and to get access to their financial and informational resources
The open-source investigation also revealed a Telegram channel “Слёзы DarkMoney,” which profiles cybercriminals. According to the channel, the Exploit forum has been fully controlled by law enforcement since July 2019 after SBU (Security Service of Ukraine), Europol, and Interpol arrested and recruited the admins. If it is confirmed to be true, one additional scenario of attacks might be added to the scene:
4) Regional law enforcement effort of combating cybercrime and destabilize the underground community
AdvIntel investigates all four possible scenarios of attack on underground forums based on the intelligence related to the compromise that was collected across DarkWeb and open source such as Telegram.
Investigative Analysis
Scenario 1
The first version observed to be widely discussed across the DarkWeb refers to the possibility of attack by hacktivists who might be working on their own or by the order of government authorities. The version is supported by the fact that stolen databases began to widely appear at open sources and might be used to de-anonymize underground forum members involved in cybercrime.
Suspicion fell on TeaMp0isoN, the team consisting of blackhats and hacktivists operating since 2009. The group is very well known for its attacks on the United Nations, NASA, NATO, Facebook, and other high-profile entities over the course of 2011 and 2012.
On February 18, 2021, TeaMp0isoN announced a hack of a similar underground forum “Unknown[.]eu,” “r00tsecurity,” and “yah-kings”.
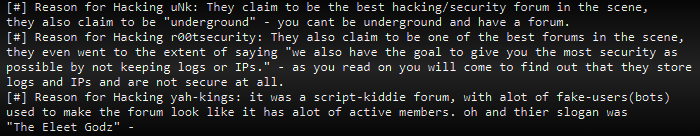
TeaMp0isoN shared an announcement of hacking of three underground forums “Unknown[.]eu”, “r00tsecurity” and “yah-kings” on December 18, 2020
Along with the announcement, the group published personal data of the members of all three DarkWeb communities including usernames, emails, passwords, and IPs.
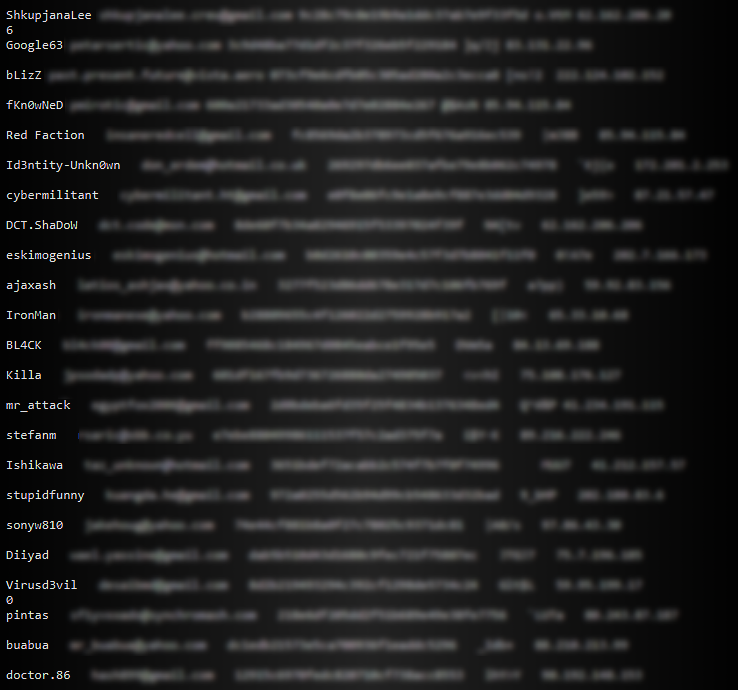
An announcement of a hack was accompanied by personal data of forums members including usernames, emails, and IPs
Scenario 2
Another possibility that has been theorized in underground communities is that the attack was perpetrated by a US law enforcement agency. This would have been an alleged retaliation to Russian cyberattacks on the US government and the business sectors.
On March 4, 2021, a threat actor operating under the alias “mcgep” (alias obfuscated) suggested that the US government had targeted underground forums in response to attacks on SolarWinds, a notable software developer that was attacked by the group of alleged state-backed Russian hackers back in December 2020.
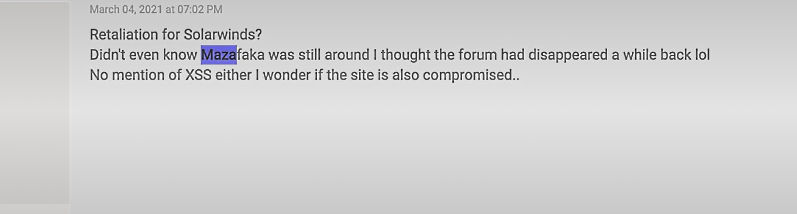
Threat actor “mcgep” suggests that the attack might be a retaliation of US law enforcement
(Source: RaidForums[.]com)
A threat actor operating under the alias “realsteel” (alias obfuscated) shared their beliefs that attacks might be a part of a global initiative against Russian-speaking cybercriminals.
“There is nothing unusual and surprising in attacks on such forums, Americans accuse Russian hackers of working with the Russian government. Therefore, it might be part of a global initiative. DarkWeb forum members should be more careful and take security measures more seriously from now on.”

Threat actor “realsteel” believes that attacks might have been a part of a global initiative against the Russian underground
(Source: exploit[.]in)
Members of RaidForums have engaged in speculating the possible motives for the attack, as well as the perpetrators. On March 4, 2021, a threat actor operating under the alias “blackjack” (alias obfuscated) went so far as to suggest banning Russian IPs from accessing the forum. This highlights the paranoia many members of these underground communities have incurred as the result of the attacks that they associated with the US law enforcement retaliation.

Threat actor “blackjack” suggested banning Russian IPs from accessing the forum in order to prevent an attack from the US law enforcement which may target the forum due to the presence of Russian-speaking cybercriminals
(Source: Raidforums[.]com)
A threat actor operating under the alias “advokat” (alias obfuscated) also supports the idea of the involvement of US law enforcement as a reaction to a continuous ransomware threat from the Russian-speaking DarkWeb community.
“This is clearly the FBI's playing on us. They understand that all cryptolockers are sitting on these forums and they got really tired of them. They have no other options besides trying to lock us up in our own environment.”
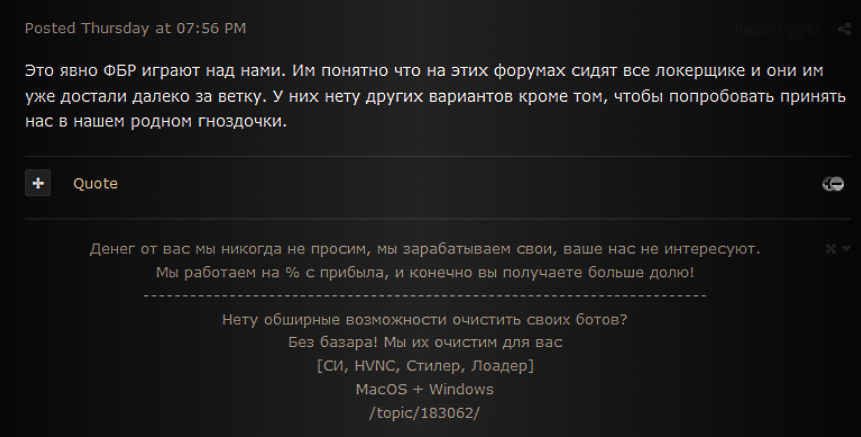
Threat actor “advokat” suggests involvement of US law enforcement in attacks on DarkWeb forums (Source: exploit[.]in)
Scenario 3
The third interpretation is an internal showdown among underground community members seeking a redistribution of power to establish control over forums and get access to their financial and informational resources.
In support of this version, forum members that performed attacks require heavy knowledge of forums' operational insights, access to the internal environment, as well as massive resources. For instance, during the attack on Exploit, intruders were able to get Exploit secure shell (SHH) access to a proxy-server hosted by Flowspec. This is used for protection from distributed denial-of-service (DDoS) attacks.
Some members advocate that an attack had been carried out by a hosting provider that might have an SSH key or passwords.
“These are not hackers, they accessed the server through SSH. Yes, this is hosting provider admins. Who else had a key? Hosters had it, am I right?”
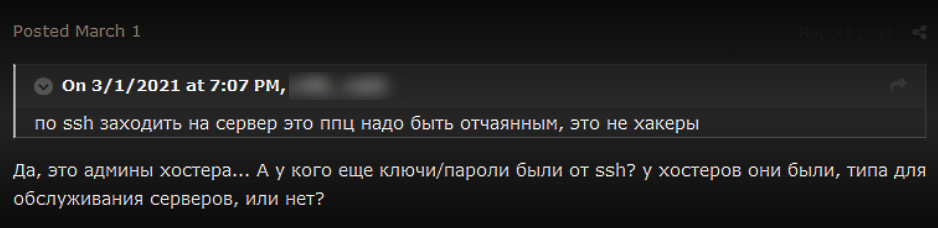
Forum member advocated that hosts might have been behind an attack on March 1, 2021
(Source: exploit[.]in)
It is worth mentioning that a Flowspec representative engaged in a conversation discussing possible upcoming attacks at the end of 2020. It became known on January 20, 2021, when the Exploit admin shared a chat history between a Flowspec representative and an underground forum member operating under the alias “agent007” (alias obfuscated). In this chat, agent007 warned the representative about an upcoming attack and recommended to “stop providing hosting service to Exploit forum”.