By Andariel Product Team & Yelisey Boguslavskiy; Head of Research

Summary: In the early Fall of 2020, AdvIntel product and research Team added Maltego transforms to our investigative arsenal. Since then, this unique tool had served as an extremely valuable component of our research, especially for DarkWeb & Ransomware investigations.
Maltego equips our cybercrime researchers with a perfect investigative tool when applied to Andariel platform datasets. These datasets contain information from numerous forums, DarkWeb communities, illicit repositories, channels, botnet infrastructures, ransomware collectives, and underground blogs. With the use of Maltego, these various datasets can work in accord, providing our investigators with 360 degrees of view over the DarkWeb and helping them to swiftly identify, assess, visualize, and prioritize the information about a certain threat.
Use Cases
For the use case demonstration, we start with the actor “Seewolf” (alias obfuscated for security purposes) a threat actor who operates within multiple communities. Their activity is also very diverse and ranges from serving as a source of news for the cybercrime community to the offers of illicitly obtained accesses and datasets. “Seewolf” targets different jurisdictions and various industries, however, the application of Maltego Tools to the Andariel datasets enabled us to swiftly and concisely organize the information on the actor and define the patterns of their activity.

Image 1: “Seewolf” activities - 360 degrees view. Maltego application enabled to swiftly divide actor’s into Red (High-Threat - illicit access and data offers) and Yellow (Moderate threat - News comments)
With the application of Maltego to Andariel datasets, we were able to quickly structure “Seewolf” posts and identify the posts which were specifically important for threat reporting.

Image 2: “Seewolf” top activities - selective view on the 3 most important threat vectors - participation in ransomware groups conversations, sales of data from stealers, and direct data leaks
With a more scoped review of the actor’s threat activities visualized in Maltego, our researchers immediately identified several crime vectors - ransomware, stealers, and data leaks. With the use of the advanced details for the entity tool, we have identified the specifics of the actor’s ransomware interest.

Image 3: Maltego Entity details tool provides a convenient structure with the most important pieces of information - in this case, forum name, URL, and the thread name
The actor’s participation in this specific forum thread was very concerning. This thread “Ransomware groups leak sites” was created on one of the largest Russian-language major forums in order to connect ransomware specialists, specifically from REvil, Egregor, and others, with talented botnet operators, network intruders, and specialists in information stealing. This was one of the efforts by the cybercrime community aiming to advance the ransomhack scheme in which ransomware affiliates steal data to publish it on their websites. Further investigation confirmed that “Seewolf” has a wast interest in the illicit data offers performed by the ransomware auctioneers.
Moreover, we have identified data sale offers for a UK bank, social media logs, Personal Identifiable Information, and an offer of the US voter data sale made by this actor:
Image 4: Maltego visualization of actor’s US voter offer
The combination of interest in ransomware data leaks, the use of stealers, and multiple sales of personal, corporate, and government data, have enabled our researchers to prioritize this actor as a credible threat that may not only be participating in the underground activities of ransomware syndicates but may offer sensitive data, including voter data to these syndicates and their affiliates. These investigative insights were proven during further actor engagement and research.
However, DarkWeb investigations were not the only applications of Maltego to our research. For instance, in the case illustrated below, Maltego was used in order to create a concise infection investigative visualization which included compromised domain, location, date, and time.
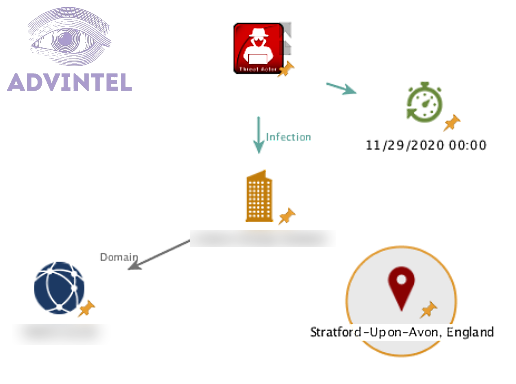
Image 5: Maltego visualization of an infection case
In another case, Maltego was used in order to portrait the actor’s tactic for the njRAT malware.

Image 6: Maltego utilization for njRAT malware Tactics Techniques & Procedures (TTPs)
Image 7: A visualization of a TrickBot case leading to a risk of ransomware deployments against religious institutions and churches in Malaysia

Image 8: Anatomy-of-Attack visualization for a QBot case against a local government institution in the United States
Investigative Conclusion: As a result of a Maltego utilization, our investigation initiated with a proper hypothesis, with the right threat assessment, and a clear understanding of the scope and scale of the threat actor activities. Maltego served as a force multiplier to our capabilities, to the Andariel DarkWeb tools, and to the efficiency and quality of our Team’s investigative operations.
Andariel users that also leverage Maltego for data-gathering and analysis are happy to know that Maltego transforms to pull data from Andariel are under development and available for use today.
Advanced Intelligence is an elite threat prevention firm. We provide our customers with access to the proprietary industry-leading “Andariel” Platform to achieve unmatched visibility into botnet breaches, underground and dark web economy and mitigate any existing or emerging threats.
Please contact us at [email protected] for the free Andariel+Maltego demonstration!