Card Enrollment Services: Highly Effective Fraud Methodology Offered in Russian Underground
Updated: Sep 4, 2020
Executive Summary
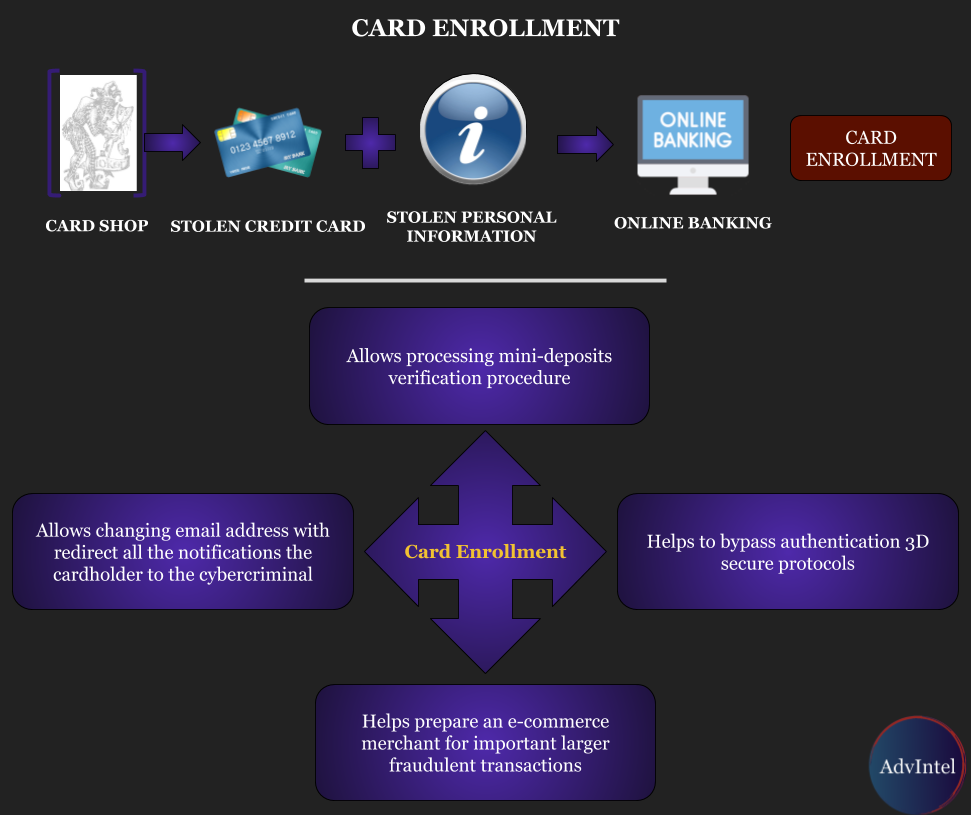
Card "enrollment" is a type of carding operation in which cybercriminals register stolen cards (primary enroll) into online banking or reset access to online banking (re-rolling) using the real name and personal information of a cardholder.
Unlike other types of fraudulent activities, in which carders leverage stolen financial information or credentials to register an entire fake, card enrollment is centered only over access to online banking leading to more criminal revenues from financial account takeover (ATO) as opposed to the other forms of fraud without online account access.
Enroll significantly assists carders in their activities. The main use of enrolling comes from the benefits provided with online banking access.
Allows carders to change billing address and phone number associated with a stolen card, therefore, the holder will not get any updates or alerts
Enables to pass mini-deposit verification
Helps bypass secure authentication protocols such as Verified-by-Visa (VBV)
Helps prepare an e-commerce merchant for important larger fraudulent transactions
Card enrollment becomes a service offered across the underground community. Cybercriminals open shops which either sell access to online banking directly or enroll cards provided to them by their carder customers.
Assessment & Findings
Advertisements of card enrollment services have been seen in the Russian-speaking underground since at least 2007. However, according to AdvIntel observation of the Russians-speaking underground forum chatter, a spike in interest to enrolling occurred in 2017 and 2018, wherein several prominent enroll services started to operate on various lower-tier Russian-speaking carding forums WWH-CLUB and Club2Crd forums. This can be explained by the intensified security measures applied by banks in recent years and the need to find novel ways to support successful purchases by criminals stealing cards. Notable enrollment services, existing for several years include FoxRoll on WWH-CLUB, 0-Day-Exploit on duplicat[.]im, Lucky Enroll on WWH-CLUB, Bad_Company Enroll on WWH- CLUB, and others.

In addition to this, forum and Telegram users started to actively share enroll manuals on underΩground and even clear web forums. Considering the structure and style, most of these manuals are likely based on WWH-CLUB enroll classes, which are a part of the forum carding training. For instance, in October 2018, a Russian-speaking threat actor “LaChe” who leverages an entry-level carding forum tenebris[.]cc to promote their carding training materials, developed a 3-stage guide on enroll, adding a discussion of potential issues with anti-fraud checks to the WWH-CLUB training.
Through the research of manuals, training guides, forum discussion, service advertisements, as well as sensitive source intelligence obtained through chat services, AdvIntel identified essential characteristics of the enroll fraud and essential traits of underground enroll offers.
Purpose of Card Rolling
Based on the observation of articles, training manuals, forum discussions, and chat- services channels, AdvIntel identified three main reasons for card enrollment:
1. Access to online banking allows for changing personal account holder information
Changing email address with redirect all the notifications on card purchases from the cardholder to the cybercriminal, and as a result, the victim will not be notified about suspicious transactions.
Changing the billing address will help to make fraudulent purchases. An online merchant usually verifies the billing address on the card and a shipping address used for purchase part of the address verification system (AVS) check. If the transaction is legitimate, the two addresses will usually be the same; however, if a transaction is fraudulent, the shipping address will be of a drop or also called a money mule. Access to online banking allows putting a drop address as the billing address.
Changing phone number also allows blocking of bank verification messages. Moreover, by putting their own phone number into online banking, criminals will be able to use this number as a legitimate verification tool. Criminals can call into the merchant’s support service, introducing themselves as a cardholder, and using the number listed in the account and notify the merchant about an expensive purchase which they plan to make from “their” card. These calls significantly decrease the possibilities of the transaction to be canceled.
2. Access to online banking allows processing mini-deposits
Mini-deposits are a verification procedure in which online service (for instance, PayPal or e-commerce platform) verifies a card through micro-transactions (typically of $1 or $2 USD). The transaction will be issued to the card, and the cardholder will need to input the exact number confirming that they have full access. Other similar verification procedures may require to enter exact card balance with will also require access to online banking.
3. Access to online banking helps to bypass authentication 3D secure protocols
3D secure protocols are an additional checking measure applied by certain banks. Usually, this includes either a VBV (Verified by Visa) or an MCSC (MasterCard Secure Code) protocol. For example, the merchant may ask to provide a VBV code during an online purchase, which will be listed in the online banking account. By having the VBV code, carders will be able to bypass a VBV verification which will greatly increase the chances of their purchase to pass through. Moreover, some merchants can be only accessed with cards that have VBV enabled.
4. Access to online banking helps prepare an e-commerce merchant for important larger fraudulent transactions
With high-end card fraud, transactions that involve expensive credit cards and purchase over several thousand USD, having online banking access becomes crucial since it provides a fraudster with intelligence regarding victim’s purchase patterns. If a high-end transaction will significantly differ from a victim’s spending pattern, anti-fraud will block it. Therefore, through re-enrolling an already used card, and resetting access to online banking, carders will receive access to the previous history of transactions and investigate it to mimic the victim behavior.
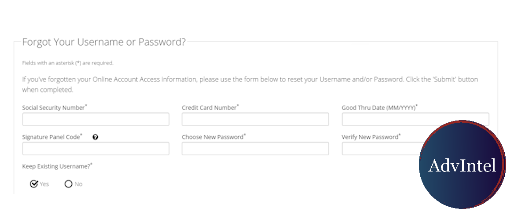
Card Rolling Process
For both primary enroll and re-enrolling a credit card underground enroll services first obtain the card itself and personal identifiable information (PII) of a cardholder. This information can be provided by a customer who makes an order at the service or can be obtained through online card skimming install, which cards are oftentimes sold on underground shops (for information on the subject, please see a Magecart case published by RisqIQ:
https://cdn.riskiq.com/wp-content/uploads/2018/11/RiskIQ-Flashpoint-Inside-MageCart-Report.pdf
Typically, the initial information includes card information: card number, expiration date, and CVV, and personal information: card holder's first and last name, address. Knowing this information, a card enroll service may use third-party services such as peoplefinders[.]com to obtain personal information. However, according to training manuals, comprehensive personal information should be obtained through underground checking services, often charging $6-7 USD per check. This information typically includes social security number, date of birth, and the up-to-date home address.
After receiving this information, the service leverages remote desktop servers (RDP) and secure shell (SSH) tunnels to create a consistent fingerprint which will correlate with cardholder's address and other information. With this digital camouflage, they access the website of the bank in which the card has been issued. If the card was not enrolled previously, they use all the obtained information to register a new online banking account, if it was, the information will be used to reset (re-enroll) the card. After this, access to online banking will be sold to an underground carding customer.
According to an article published on an underground Telegram community “Basta” in July 2017, all commercial card enroll services will always provide their customers with access to the SSH tunnel or remote desktop server (RDP), through which the card was initially enrolled. This creates consistency between digital fingerprints of merchant initially accessing the bank for enrollment and its customer accessing the online banking.
Conclusion
Card enrollment-as-a-service remains a prominent part of an underground economy. As security measures such as 3D protocols, verification calls, email notifications, and others complicate carder activities, ways to bypass such measures will become more popular. Getting access to a credit card online banking through enrollment and further manipulations with this card is a very volatile process involving numerous nuances. AdvIntel observes an increasing interest in customizing enroll solutions by cybercriminals, willing to increase the number of enrolled cards that they can offer for sale. This may include creating a list of “golden” BINs for specific banks, finding glitches in online registration systems for a specific institution, or developing a targeted approach for each bank. AdvIntel will continue to provide intelligence information for these specific enroll fraud schemes.